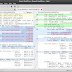
CANalyzat0r - Security Analysis Toolkit For Proprietary Car Protocols
This software project is a result of a Bachelor's thesis created at SCHUTZWERK in collaboration with Aalen University by Philipp Schmied.
Please refer to the corresponding blog post for more information.
Why another CAN tool?
- Built from scratch with new ideas for analysis mechanisms
- Bundles features of many other tools in one place
- Modular and extensible: Read the docs and implement your own analysis mechanisms
- Comfortable analysis using a GUI
- Manage work in separate projects using a database
- Documentation: Read the docs if you need a manual or technical info.
Installing and running:
- Run
sudo ./install_requirements.shalong withsudo -E ./CANalyzat0r.sh. This will create a folder calledpipenvwith apipenvenvironment in it. - Or just use the docker version which is recommended at this time (Check the
README.mdfile in the subdirectory)
./doc/build folder.Features
- Manage interface configuration (automatic loading of kernel modules, manage physical and virtual SocketCAN devices)
- Multi interface support
- Manage your work in projects. You can also import and export them in the human readable/editable JSON format
- Logging of all actions
- Graphical sniffing
- Manage findings, dumps and known packets per project
- Easy copy and paste between tabs. Also, you can just paste your SocketCAN files into a table that allows pasting
- Threaded Sending, Fuzzing and Sniffing
- Sniffing at the same time
Testing It
You can use the Instrument Cluster Simulator in order to tinker with a virtual CAN bus without having to attach real CAN devices to your machine.
Troubleshooting
Empty GUI Windows
Please make sure that the
QT_X11_NO_MITSHM environment variable is set to 1. When using sudo, please include the -E option in order to preserve this environment variable as follows: sudo -E ./CANalyzat0r.sh.Fixing the GUI style
This application has to be run as superuser. Because of a missing configuration, the displayed style can be set to an unwanted value when the effective UID is 0. To fix this behaviour, follow these steps:
- Quick way: Execute
echo "[QT]\nstyle=CleanLooks" >> ~/.config/Trolltech.conf
- Alternative way:
- Install qt4-qtconfig:
sudo apt-get install qt4-qtconfig - Run qtconfig-qt4 as superuser and change the GUI style to CleanLooks or GTK+
- Install qt4-qtconfig:
- Or use the docker container
Via: feedproxy.google.com
CANalyzat0r - Security Analysis Toolkit For Proprietary Car Protocols
 Reviewed by Anónimo
on
17:47
Rating:
Reviewed by Anónimo
on
17:47
Rating:
 Reviewed by Anónimo
on
17:47
Rating:
Reviewed by Anónimo
on
17:47
Rating: