Vulnado - Purposely Vulnerable Java Application To Help Lead Secure Coding Workshops
This application and exercises will take you through some of the OWASP top 10 Vulnerabilities and how to prevent them.
Up and running
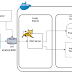
Architecture
The docker network created by
Exercises
Up and running
- Install Docker for MacOS or Windows. You'll need to create a Docker account if you don't already have one.
git clone git://github.com/ScaleSec/vulnadocd vulnadodocker-compose up- Open a browser and navigate to the client to make sure it's working: http://localhost:1337
- Then back in your terminal verify you have connection to your API server:
nc -vz localhost 8080
Architecture
The docker network created by
docker-compose maps pretty well to a multi-tier architecture where a web server is publicly available and there are other network resources like a database and internal site that are not publicly available.Exercises
- SQL Injection
- XSS - Cross Site Scripting
- SSRF - Server Side Request Forgery
- RCE - Remote Code Execution & Reverse Shell
Via: feedproxy.google.com
Vulnado - Purposely Vulnerable Java Application To Help Lead Secure Coding Workshops
 Reviewed by Anónimo
on
18:29
Rating:
Reviewed by Anónimo
on
18:29
Rating:
 Reviewed by Anónimo
on
18:29
Rating:
Reviewed by Anónimo
on
18:29
Rating:


