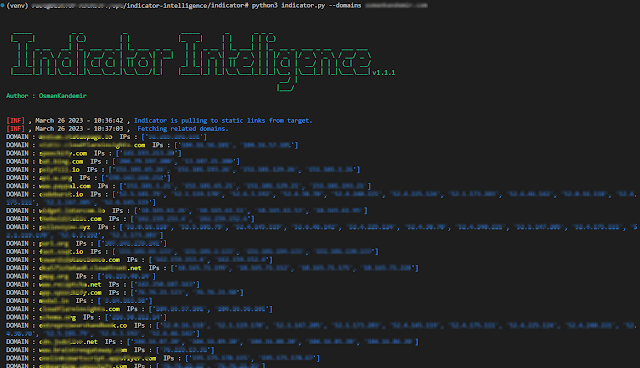
Indicator-Intelligence - Finds Related Domains And IPv4 Addresses To Do Threat Intelligence After Indicator-Intelligence Collects Static Files
Finds related domains and IPv4 addresses to do threat intelligence after Indicator-Intelligence collects static files.
Done
- Related domains, IPs collect
Installation
From Source Code
You can use virtualenv for package dependencies before installation.
git clone https://github.com/OsmanKandemir/indicator-intelligence.gitcd indicator-intelligencepython setup.py buildpython setup.py installFrom Pypi
The script is available on PyPI. To install with pip:
pip install indicatorintelligenceFrom Dockerfile
You can run this application on a container after build a Dockerfile.
docker build -t indicator .docker run indicator --domains target-web.com --jsonFrom DockerHub
docker pull osmankandemir/indicatordocker run osmankandemir/indicator --domains target-web.com --jsonFrom Poetry
pip install poetrypoetry installUsage
-d DOMAINS [DOMAINS], --domains DOMAINS [DOMAINS] Input Targets. --domains target-web1.com target-web2.com-p PROXY, --proxy PROXY Use HTTP proxy. --proxy 0.0.0.0:8080-a AGENT, --agent AGENT Use agent. --agent 'Mozilla/5.0 (Windows NT 10.0; Win64; x64)'-o JSON, --json JSON JSON output. --jsonFunction Usage
See; CONTRIBUTING.md
License
Copyright (c) 2023 Osman Kandemir
Licensed under the GPL-3.0 License.
Donations
If you like Indicator-Intelligence and would like to show support, you can use Buy A Coffee or Github Sponsors feature for the developer using the button below.
You can use the github sponsored tiers feature for purchasing and other features.
Sponsor me : https://github.com/sponsors/OsmanKandemir
Via: www.kitploit.com
 Reviewed by Zion3R
on
20:20
Rating:
Reviewed by Zion3R
on
20:20
Rating: